
What is consent phishing (and how can you avoid it)?
Scammers are always looking for new ways to breach security measures as they are improved. While more platforms are adding support for Multi-factor Authentication (MFA), scammers have now found a way around it, called consent phishing.
How Attackers Steal Sensitive Data
Attackers usually start by registering an app with an OAuth 2.0 provider, such as Microsoft’s Azure Active Directory. The attacker will make sure the app looks trustworthy. They might use the name of a well-known product, or an association with a particular respected brand.
The attacker then creates a link to this app, which can be sent through a phishing email or a compromised website or a fake landing page. If the user clicks the link, they will see an authentic consent prompt asking them to grant the malicious app permissions to data.
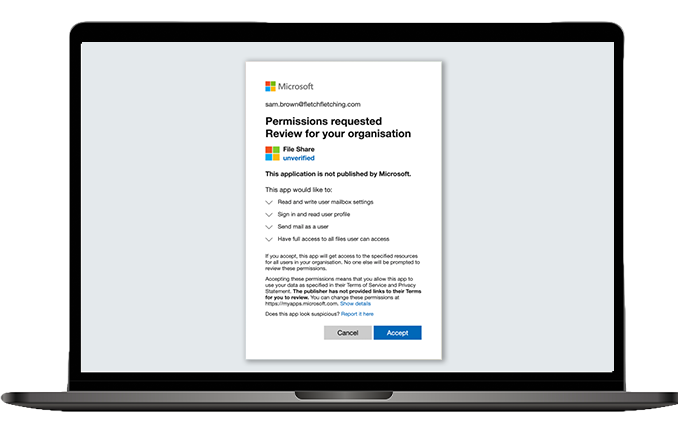
If the user clicks accept, they will unwittingly grant the app permission to access sensitive data. The app gets an authorization code, which it redeems for an access token, and potentially a refresh token. The access token is used to make API calls on behalf of the user.
In a nutshell, that means you’ve granted the attacker permanent access to your account, which they retain even if you change your password or have MFA enabled.
You can revoke access, but you’d need to know something fishy was happening to think about doing that. The truth is that most people don’t check very often which apps have access to their accounts. We are able to identify and take measures to remediate malicious apps by disabling them and preventing users from accessing them. In some instances, we’ve also taken legal action to further protect our customers.
Measures to Prevent and Remediate
Microsoft has been working to secure its application ecosystem, disabling malicious apps and even taking legal action where required. It suggests that organisations educate their people on consent phishing tactics and how to avoid them, including how to identify and avoid phishing emails. It also advises carefully checking all domain names (a single letter’s difference can take you to a dodgy domain) and promoting the use of applications that have been publisher verified.
Microsoft suggests organisations configure application consent policies by allowing users to only consent to specific applications they trust.
Numata Business IT can help your business to combat advanced cybersecurity attacks. Get in touch today to find out more.

