Beware of this legit-looking COVID-19 scam
Liza Weschta, Cybersecurity Product Manager at Numata Business IT, received a legitimate-looking COVID-19 phishing scam/ business email compromise (BEC) attack.
The email looks as though it comes from the Gauteng Health Department regarding COVID-19 vaccination, complete with the legitimate logos and email signatures one would expect to see in an official provincial government email.
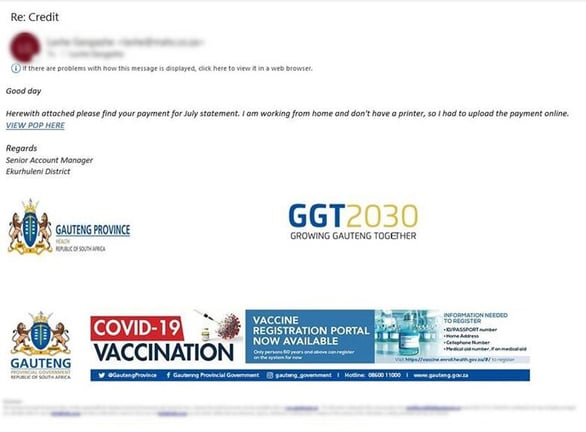
“The email address I received the email from has obviously been breached and the cybercriminal is sending out emails from this inbox,” Liza says. “That’s why this email passed DKIM and DMARC rules and this got through our Microsoft Exchange Online Security Protection.”
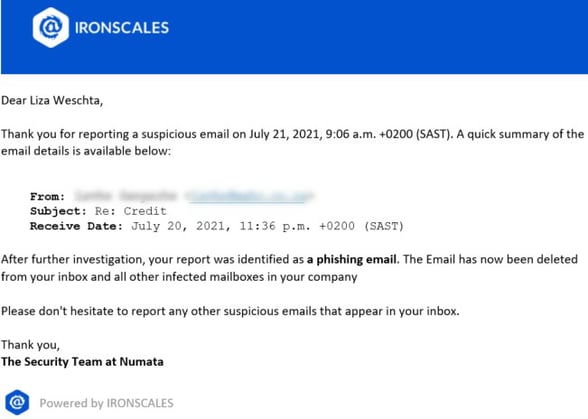
She says there’s also been a recent surge in domain creation BEC attacks occurring in both our own environment as well as our client's environment. “Most of these have similar characteristics and a call to “'VIEW PROOF OF PAYMENT HERE', which is a malicious social engineering attack", she says. “This is where we use an advanced internal anti-phishing tool, called Ironscales. With a click of a button, I reported the phishing email in my Ironscales toolbar and within seconds the Ironscales virtual AI security analyst identified it as a phishing email and remediated it by deleting the email from my mailbox, and the same email from any other infected mailboxes in the company.”
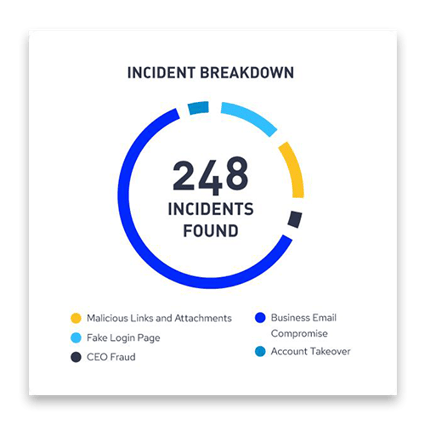
“Ironscales can save a business time (especially an enterprise organisation) on inbound email threat remediation and AI-assisted phishing classification,” Liza says. “It can cluster bad emails at scale – instantly. Research has shown it takes 82 seconds from the distribution time till the usual attack has its first victim.”
She notes that many cybercriminals have moved away from malware-based email attacks to unleashing billions upon billions of more advanced attacks like BEC, advanced takeover, VIP impersonation, and credential harvesting using fake landing pages.
Why do customers still need Advanced Email Threat Protection and DMARC?
Domain-based Message Authentication, Reporting, and Conformance (DMARC) is an email authentication method that mail administrators use to prevent hackers and other attackers from impersonating their domain. But Liza says that while DMARC will stop many impersonations (exact domain impersonations), it can’t help you to avoid other types of phishing, such as display name impersonation, cousin domain impersonation, spoofing and BEC.
“These will bypass technical controls and can land within the business. Ironscales detects domain impersonations, where DMARC won’t,” she says. DMARC is also heavily reliant on SPF and DKIM configuration, which is a policy that both the sender and receiver need to enable. As reported by Help Net Security, 99% of all domains worldwide do not comply with this protocol, so if you deal with customers, vendors and third parties who may not have this configured correctly, it becomes a redundant email policy control and therefore does not work. Additionally, DMARC still does not help with detecting, preventing and automatically remediating phishing attacks
Ironscales also unite human and machine intelligence. “Controls alone are not enough, as email phishing is a human and machine problem that requires a human and machine solution,” says Liza.
When layered into a holistic defence system, employees can become a vital layer of detection and contribute to the growing effectiveness of machine learning models. AI coupled with user controls/human intelligence is the right combination to fight the sophisticated attacks taking place today.
Get a free 90-Day scan back to highlight risks in your inbox!